considered the gravity of cyber breaches?
know hackers can access your data?
Concerned about your children's online safety?
Embark on a transformative journey with us! Signing up unlocks a world of cutting-edge courses, certifications, and a spectrum of valuable resources for an entire year. Elevate your skills, boost your career, and stay ahead in the dynamic realm of cybersecurity.
Exclusive Access: Gain privileged access to our extensive library of courses, workshops, and certifications. Dive into a treasure trove of knowledge curated by industry experts.
Accelerate Your Career: Equip yourself with the latest insights and practical skills that employers value. Stay at the forefront of the ever-evolving cybersecurity landscape.
Continuous Learning: Enjoy a year-long learning journey with regular updates, new courses, and dynamic content designed to keep your skills sharp and up-to-date.
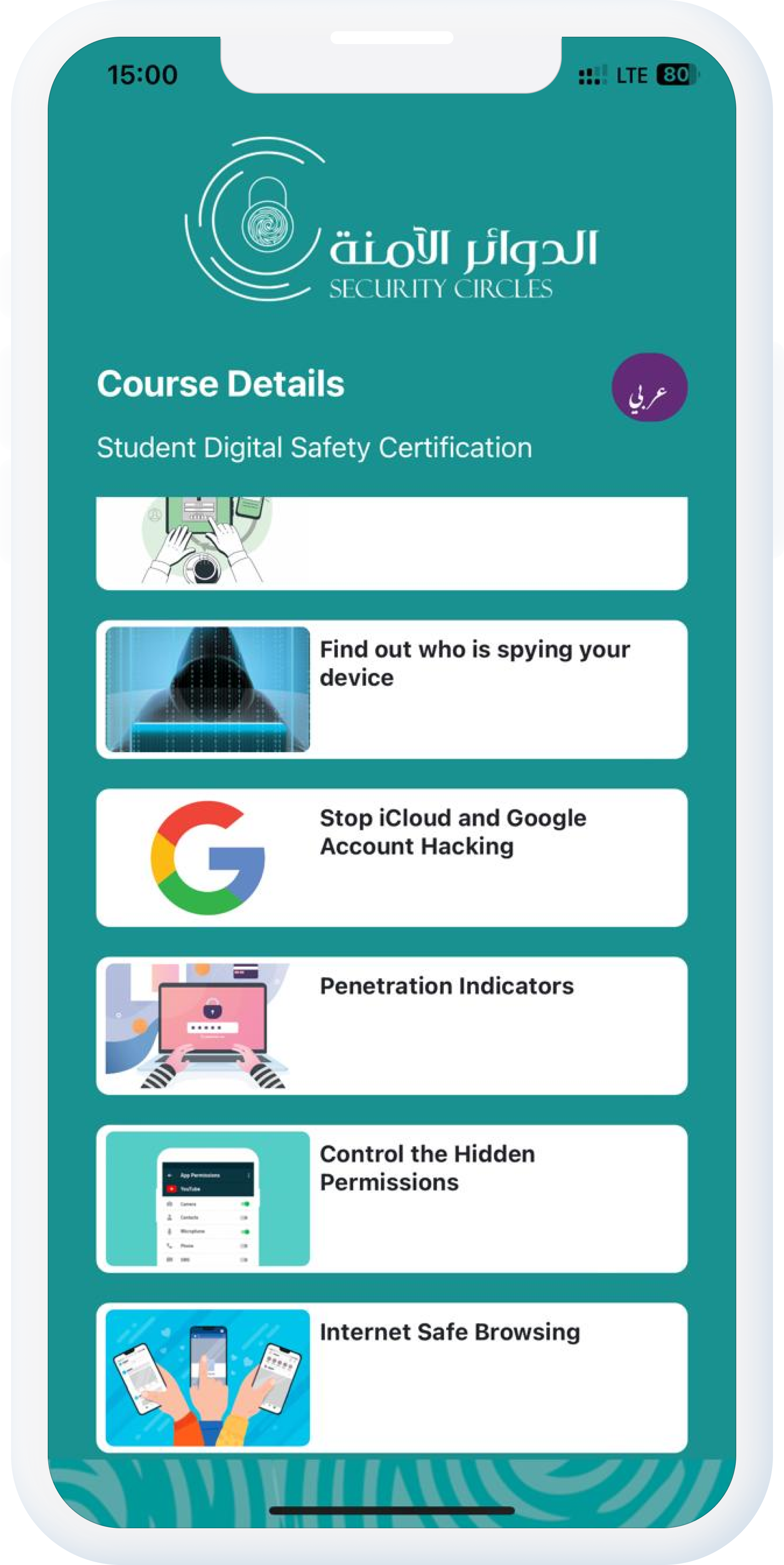
Dive into the world of information security, exploring its definition, goals, and key aspects. This training also provides an overview of the curriculum's contents and helps assess your current knowledge in the cybersecurity field.
01Achieving leadership in the eld of digital safety for the categories of education by providing information, tools, and resources consistent with the needs of each category.
02Enabling the education categories with su cient skills to deal with the digital world to maximize the bene t and reduce risks in an advanced knowledge learning society. .
03

Early identification of intrusion attempts enhances user protection and safeguards privacy.
04Discover the advantages of having an iCloud account and the potential risks of sharing access with others. Additionally, learn how to prevent unauthorized access to this crucial personal account.
05Learn to anticipate breaches based on specific indicators to better address and halt potential security threats.
06Learn how to control permissions to eliminate numerous intrusions and malicious programs that threaten user privacy.
07Learn about phishing websites and how to avoid them while browsing various internet pages.
081. Sign Up: Provide your name, email, and create a secure password to begin your journey.
2. Payment: Proceed securely to pay $10 to unlock all courses for the whole year. Our platform ensures the safety of your transactions with trusted payment gateways.
3. Get Your Student ID: Upon payment confirmation, instantly receive your unique Student ID. This ID grants you access to our platform and allows you to track your progress effortlessly.
4. Login & Explore: Log in with your credentials to our mobile application and step into a world of knowledge. Navigate through our diverse courses, engage with fellow learners, and take control of your professional growth.
If you encounter any issues during sign-up or payment, or if you have any feedback or complaints, please write to us or fill out the form below. We're here to help!
For inquiries and more information about our services and training courses, please do not hesitate to contact us.

Security Circle App is just a tap away — Get it on the App Store or Google Play

Copyright 2022 Security Circles. Developed By Enad abuzaid